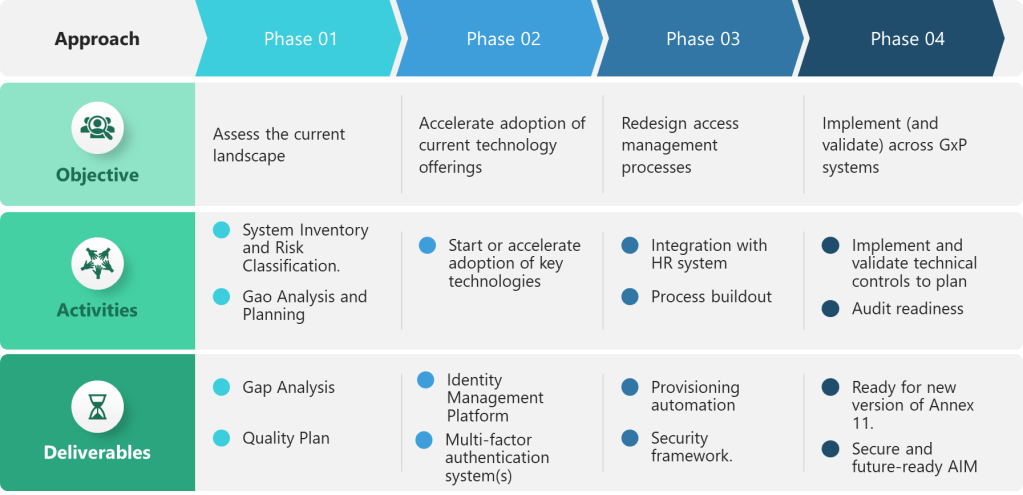
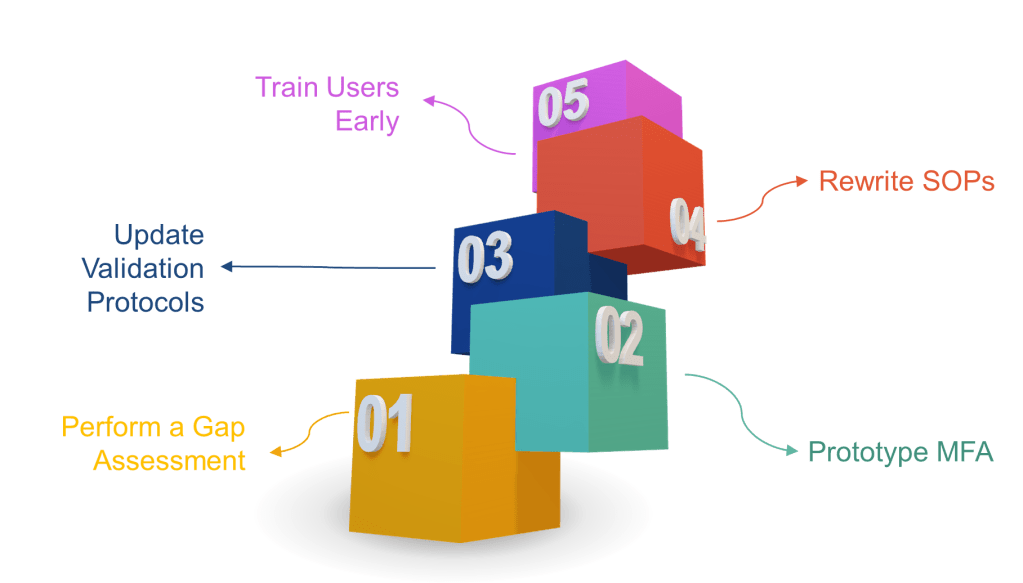
In the annals of pharmaceutical regulation, few acronyms have generated as much discussion, confusion, and controversy as ALCOA. What began as a simple mnemonic device for FDA inspectors in the 1990s has evolved into a complex framework that has sparked heated debates across regulatory agencies, industry associations, and boardrooms worldwide. The story of ALCOA’s evolution from a five-letter inspector’s tool to the comprehensive ALCOA++ framework represents one of the most significant regulatory harmonization challenges of the modern pharmaceutical era.
With the publication of Draft EU GMP Chapter 4 in 2025, this three-decade saga of definitional disputes, regulatory inconsistencies, and industry resistance finally reaches its definitive conclusion. For the first time in regulatory history, a major jurisdiction has provided comprehensive, legally binding definitions for all ten ALCOA++ principles, effectively ending years of interpretive debates and establishing the global gold standard for pharmaceutical data integrity.
The Genesis: Stan Woollen’s Simple Solution
The ALCOA story begins in the early 1990s with Stan W. Woollen, an FDA inspector working in the Office of Enforcement. Faced with the challenge of training fellow GLP inspectors on data quality assessment, Woollen needed a memorable framework that could be easily applied during inspections. Drawing inspiration from the ubiquitous aluminum foil manufacturer, he created the ALCOA acronym: Attributable, Legible, Contemporaneous, Original, and Accurate.
“The ALCOA acronym was first coined by me while serving in FDA’s Office of Enforcement back in the early 1990’s,” Woollen later wrote in a 2010 retrospective. “Exactly when I first used the acronym I don’t recall, but it was a simple tool to help inspectors evaluate data quality”.
Woollen’s original intent was modest—create a practical checklist for GLP inspections. He explicitly noted that “the individual elements of ALCOA were already present in existing Good Manufacturing Practice (GMP) and GLP regulations. What he did was organize them into an easily memorized acronym”. This simple organizational tool would eventually become the foundation for a global regulatory framework.
The First Expansion: EMA’s ALCOA+ Revolution
The pharmaceutical landscape of 2010 bore little resemblance to Woollen’s 1990s GLP world. Electronic systems had proliferated, global supply chains had emerged, and data integrity violations were making headlines. Recognizing that the original five ALCOA principles, while foundational, were insufficient for modern pharmaceutical operations, the European Medicines Agency took a bold step.
In their 2010 “Reflection paper on expectations for electronic source data and data transcribed to electronic data collection tools in clinical trials,” the EMA introduced four additional principles: Complete, Consistent, Enduring, and Available—creating ALCOA+. This expansion represented the first major regulatory enhancement to Woollen’s original framework and immediately sparked industry controversy.
The Industry Backlash
The pharmaceutical industry’s response to ALCOA+ was swift and largely negative. Trade associations argued that the original five principles were sufficient and that additional requirements represented regulatory overreach. “The industry argued that the original 5 were sufficient; regulators needed modern additions,” as contemporary accounts noted.
The resistance wasn’t merely philosophical—it was economic. Each new principle required system validations, process redesigns, and staff retraining. For companies operating legacy paper-based systems, the “Enduring” and “Available” requirements posed particular challenges, often necessitating expensive digitization projects.
The Fragmentation: Regulatory Babel
What followed ALCOA+’s introduction was a period of regulatory fragmentation that would plague the industry for over a decade. Different agencies adopted different interpretations, creating a compliance nightmare for multinational pharmaceutical companies.
FDA’s Conservative Approach
The FDA, despite being the birthplace of ALCOA, initially resisted the European additions. Their 2016 “Data Integrity and Compliance with CGMP Guidance for Industry” focused primarily on the original five ALCOA principles, with only implicit references to the additional requirements8. This created a transatlantic divide where companies faced different standards depending on their regulatory jurisdiction.
MHRA’s Independent Path
The UK’s MHRA further complicated matters by developing their own interpretations in their 2018 “GxP Data Integrity Guidance.” While generally supportive of ALCOA+, the MHRA included unique provisions such as their emphasis on “permanent and understandable” under “legible,” creating yet another variant.
WHO’s Evolving Position
The World Health Organization initially provided excellent guidance in their 2016 document, which included comprehensive ALCOA explanations in Appendix 1. However, their 2021 revision removed much of this detail.
PIC/S Harmonization Attempt
The Pharmaceutical Inspection Co-operation Scheme (PIC/S) attempted to bridge these differences with their 2021 “Guidance on Data Integrity,” which formally adopted ALCOA+ principles. However, even this harmonization effort failed to resolve fundamental definitional inconsistencies between agencies.
The Traceability Controversy: ALCOA++ Emerges
Just as the industry began adapting to ALCOA+, European regulators introduced another disruption. The EMA’s 2023 “Guideline on computerised systems and electronic data in clinical trials” added a tenth principle: Traceability, creating ALCOA++.
The Redundancy Debate
The addition of Traceability sparked the most intense regulatory debate in ALCOA’s history. Industry experts argued that traceability was already implicit in the original ALCOA principles. As R.D. McDowall noted in Spectroscopy Online, “Many would argue that the criterion ‘traceable’ is implicit in ALCOA and ALCOA+. However, the implication of the term is the problem; it is always better in data regulatory guidance to be explicit”.
The debate wasn’t merely academic. Companies that had invested millions in ALCOA+ compliance now faced another round of system upgrades and validations. The terminology confusion was equally problematic—some agencies used ALCOA++, others preferred ALCOA+ with implied traceability, and still others created their own variants like ALCOACCEA.
Industry Frustration
By 2023, industry frustration had reached a breaking point. Pharmaceutical executives complained about “multiple naming conventions (ALCOA+, ALCOA++, ALCOACCEA) created market confusion”. Quality professionals struggled to determine which version applied to their operations, leading to over-engineering in some cases and compliance gaps in others.
The regulatory inconsistencies created particular challenges for multinational companies. A facility manufacturing for both US and European markets might need to maintain different data integrity standards for the same product, depending on the intended market—an operationally complex and expensive proposition.
The Global Harmonization Failure
Despite multiple attempts at harmonization through ICH, PIC/S, and bilateral agreements, the regulatory community failed to establish a unified ALCOA standard. Each agency maintained sovereign authority over their interpretations, leading to:
Definitional Inconsistencies: The same ALCOA principle had different definitions across agencies. “Attributable” might emphasize individual identification in one jurisdiction while focusing on system traceability in another.
Technology-Specific Variations: Some agencies provided technology-neutral guidance while others specified different requirements for paper versus electronic systems.
Enforcement Variations: Inspection findings varied significantly between agencies, with some inspectors focusing on traditional ALCOA elements while others emphasized ALCOA+ additions.
Economic Inefficiencies: Companies faced redundant validation efforts, multiple audit preparations, and inconsistent training requirements across their global operations.
Draft EU Chapter 4: The Definitive Resolution
Against this backdrop of regulatory fragmentation and industry frustration, the European Commission’s Draft EU GMP Chapter 4 represents a watershed moment in pharmaceutical regulation. For the first time in ALCOA’s three-decade history, a major regulatory jurisdiction has provided comprehensive, legally binding definitions for all ten ALCOA++ principles.
Comprehensive Definitions
The draft chapter doesn’t merely list the ALCOA++ principles—it provides detailed, unambiguous definitions for each. The “Attributable” definition spans multiple sentences, covering not just identity but also timing, change control, and system attribution. The “Legible” definition explicitly addresses dynamic data and search capabilities, resolving years of debate about electronic system requirements.
Technology Integration
Unlike previous guidance documents that treated paper and electronic systems separately, Chapter 4 provides unified definitions that apply regardless of technology. The “Original” definition explicitly addresses both static (paper) and dynamic (electronic) data, stating that “Information that is originally captured in a dynamic state should remain available in that state”.
Risk-Based Framework
The draft integrates ALCOA++ principles into a broader risk-based data governance framework, addressing long-standing industry concerns about proportional implementation. The risk-based approach considers both data criticality and data risk, allowing companies to tailor their ALCOA++ implementations accordingly.
Hybrid System Recognition
Acknowledging the reality of modern pharmaceutical operations, the draft provides specific guidance for hybrid systems that combine paper and electronic elements—a practical consideration absent from earlier ALCOA guidance.
The End of Regulatory Babel
Draft Chapter 4’s comprehensive approach should effectively ends the definitional debates that have plagued ALCOA implementation for over a decade. By providing detailed, legally binding definitions, the EU has created the global gold standard that other agencies will likely adopt or reference.
Global Influence
The EU’s pharmaceutical market represents approximately 20% of global pharmaceutical sales, making compliance with EU standards essential for most major manufacturers. When EU GMP requirements are updated, they typically influence global practices due to the market’s size and regulatory sophistication.
Regulatory Convergence
Early indications suggest other agencies are already referencing the EU’s ALCOA++ definitions in their guidance development. The comprehensive nature of Chapter 4’s definitions makes them attractive references for agencies seeking to update their own data integrity requirements.
Industry Relief
For pharmaceutical companies, Chapter 4 represents regulatory clarity after years of uncertainty. Companies can now design global data integrity programs based on the EU’s comprehensive definitions, confident that they meet or exceed requirements in other jurisdictions.
Lessons from the ALCOA Evolution
The three-decade evolution of ALCOA offers several important lessons for pharmaceutical regulation:
- Organic Growth vs. Planned Development: ALCOA’s organic evolution from inspector tool to global standard demonstrates how regulatory frameworks can outgrow their original intent. The lack of coordinated development led to inconsistencies that persisted for years.
- Industry-Regulatory Dialogue Importance: The most successful ALCOA developments occurred when regulators engaged extensively with industry. The EU’s consultation process for Chapter 4, while not without controversy, produced a more practical and comprehensive framework than previous unilateral developments.
- Technology Evolution Impact: Each ALCOA expansion reflected technological changes in pharmaceutical manufacturing. The original principles addressed paper-based GLP labs, ALCOA+ addressed electronic clinical systems, and ALCOA++ addresses modern integrated manufacturing environments.
- Global Harmonization Challenges: Despite good intentions, regulatory harmonization proved extremely difficult to achieve through international cooperation. The EU’s unilateral approach may prove more successful in creating de facto global standards.
The Future of Data Integrity
With Draft Chapter 4’s comprehensive ALCOA++ framework, the regulatory community has finally established a mature, detailed standard for pharmaceutical data integrity. The decades of debate, expansion, and controversy have culminated in a framework that addresses the full spectrum of modern pharmaceutical operations.
Implementation Timeline
The EU’s implementation timeline provides the industry with adequate preparation time while establishing clear deadlines for compliance. Companies have approximately 18-24 months to align their systems with the new requirements, allowing for systematic implementation without rushed remediation efforts.
Global Adoption
Early indications suggest rapid global adoption of the EU’s ALCOA++ definitions. Regulatory agencies worldwide are likely to reference or adopt these definitions in their own guidance updates, finally achieving the harmonization that eluded the international community for decades.
Technology Integration
The framework’s technology-neutral approach while addressing specific technology requirements positions it well for future technological developments. Whether dealing with artificial intelligence, blockchain, or yet-to-be-developed technologies, the comprehensive definitions provide a stable foundation for ongoing innovation.
Conclusion: From Chaos to Clarity
The evolution of ALCOA from Stan Woollen’s simple inspector tool to the comprehensive ALCOA++ framework represents one of the most significant regulatory development sagas in pharmaceutical history. Three decades of expansion, controversy, and fragmentation have finally culminated in the European Union’s definitive resolution through Draft Chapter 4.
For an industry that has struggled with regulatory inconsistencies, definitional debates, and implementation uncertainties, Chapter 4 represents more than just updated guidance—it represents regulatory maturity. The comprehensive definitions, risk-based approach, and technology integration provide the clarity that has been absent from data integrity requirements for over a decade.
The pharmaceutical industry can now move forward with confidence, implementing data integrity programs based on clear, comprehensive, and legally binding definitions. The era of ALCOA debates is over; the era of ALCOA++ implementation has begun.
As we look back on this regulatory journey, Stan Woollen’s simple aluminum foil-inspired acronym has evolved into something he likely never envisioned—a comprehensive framework for ensuring data integrity across the global pharmaceutical industry. The transformation from inspector’s tool to global standard demonstrates how regulatory innovation, while often messy and contentious, ultimately serves the critical goal of ensuring pharmaceutical product quality and patient safety.
The Draft EU Chapter 4 doesn’t just end the ALCOA debates—it establishes the foundation for the next generation of pharmaceutical data integrity requirements. For an industry built on evidence and data, having clear, comprehensive standards for data integrity represents a fundamental advancement in regulatory science and pharmaceutical quality assurance.
References
- https://aardexgroup.com/alcoa/
- https://arkivum.com/blog/alcoa-the-cornerstone-of-data-integrity-in-life-sciences/
- https://blog.pqegroup.com/clinical-studies/ema-publishes-guideline-on-computerized-systems-and-electronic-data-in-clinical-trials
- https://chemignition.com/blog/alcoa-pharma
- https://gabi-journal.net/pharmaceutical-data-integrity-issues-challenges-and-proposed-solutions-for-manufacturers-and-inspectors.html
- https://good.laboratorypractice.com/what-is-alcoa/
- https://health.ec.europa.eu/document/download/fa336a6e-753b-46fc-b53b-9178bacd8878_en?filename=mp_vol4_chap4_consultation_guideline_en.pdf
- https://ispe.org/pharmaceutical-engineering/ispeak/dynamic-data-integrity-why-alcoa-keeps-evolving
- https://kneat.com/article/data-integrity-alcoa-plus-plus/
- https://member.pharmastate.academy/from-alcoa-to-alcoa-plus-data-integrity/
- https://mmsholdings.com/perspectives/ema-guidelines-electronic-data-clinical-trials/
- https://pharmabeginers.com/alcoa-alco-principle-data-integrity/
- https://pharmastate.academy/from-alcoa-to-alcoa-plus-data-integrity/
- https://picscheme.org/docview/4234
- https://pubmed.ncbi.nlm.nih.gov/29158286/
- https://qscompliance.com/wp-content/uploads/2019/01/ALCOA-Principles.pdf
- https://redica.com/the-o-in-alcoa/
- https://rx-360.org/wp-content/uploads/2018/08/Data-Quality-and-the-Origin-of-ALCOA-by-Stan-Woolen-2010.pdf
- https://valsource.com/resource-center/valid-insights/5-notorious-compliance-issues-in-the-pharmaceutical-industry-and-how-to-avoid-them/
- https://www.biopharminternational.com/view/alcoa-and-data-integrity-0
- https://www.clinical.ly/alcoa-and-data-integrity-in-clinical-trials/
- https://www.cognidox.com/blog/data-integrity-alcoa-principles
- https://www.compliancequest.com/blog/fda-who-uk-mhra-data-integrity-guidelines/
- https://www.ema.europa.eu/en/documents/regulatory-procedural-guideline/guideline-computerised-systems-and-electronic-data-clinical-trials_en.pdf
- https://www.ema.europa.eu/en/human-regulatory-overview/research-development/compliance-research-development/good-manufacturing-practice/guidance-good-manufacturing-practice-good-distribution-practice-questions-answers
- https://www.fda.gov/files/drugs/published/Data-Integrity-and-Compliance-With-Current-Good-Manufacturing-Practice-Guidance-for-Industry.pdf
- https://www.fdli.org/2019/05/communicating-with-fda-when-data-integrity-issues-arise-during-clinical-trials/
- https://www.gmp-compliance.org/gmp-news/alcoa-what-does-it-mean
- https://www.gmp-compliance.org/gmp-news/final-gcp-guideline-on-computerized-systems-and-data-integrity
- https://www.gmp-journal.com/current-articles/details/are-data-quality-and-alcoa-attributes-equivalent.html
- https://www.ijpsjournal.com/article/Data+Integrity+breach+A+critical+challenge+faced+by+the+pharmaceutical+industry+throughout+the+regulatory+audit
- https://www.mastercontrol.com/gxp-lifeline/uks-mhra-issues-final-guidance-on-gxp-data-integrity/
- https://www.numberanalytics.com/blog/regulatory-framework-data-integrity
- https://www.pda.org/docs/default-source/website-document-library/chapters/presentations/brazil/pharma-trends-day-1/data-integrity-case-studies.pdf?sfvrsn=57f6838e_1
- https://www.pharmaceuticalonline.com/doc/these-were-fda-s-top-citation-issues-for-data-quality-in-0001
- https://www.pharmaguideline.com/2018/12/alcoa-to-alcoa-plus-for-data-integrity.html
- https://www.pharmtech.com/view/alcoa-and-data-integrity
- https://www.quanticate.com/blog/alcoa-principles
- https://www.sciencedirect.com/science/article/pii/S2949866X24001060
- https://www.scilife.io/blog/regulators-data-integrity
- https://www.scilife.io/glossary/alcoa
- https://www.spectroscopyonline.com/view/data-quality-and-data-integrity-are-same-right-wrong
- https://www.spectroscopyonline.com/view/is-traceability-the-glue-for-alcoa-alcoa-or-alcoa-
- https://www.tabletscapsules.com/3641-Technical-Articles/594926-Data-Integrity-Stepping-up-to-Scrutiny-in-the-Dietary-Supplement-Industry/
- https://www.thepharmajournal.com/archives/2017/vol6issue2/PartB/6-2-6-428.pdf
- https://www.valgenesis.com/blog/6-best-practices-for-alcoa-data-integrity-success
- https://www.ympronta.it/blog/ympronta-blog-1/data-integrity-in-pharmaceutical-industry-2
- https://www.youtube.com/watch?v=PNw-KcGbFjo