I have realized I need to build a Part 11 and Annex 11 course. I’ve evaluated some external offerings and decided they really lack that applicability layer, which I am going to focus on.
Here are my draft learning objectives.
21 CFR Part 11 Learning Objectives
- Understanding Regulatory Focus: Understand the current regulatory focus on data integrity and relevant regulatory observations.
- FDA Requirements: Learn the detailed requirements within Part 11 for electronic records, electronic signatures, and open systems.
- Implementation: Understand how to implement the principles of 21 CFR Part 11 in both computer hardware and software systems used in manufacturing, QA, regulatory, and process control.
- Compliance: Learn to meet the 21 CFR Part 11 requirements, including the USFDA interpretation in the Scope and Application Guidance.
- Risk Management: Apply the current industry risk-based good practice approach to compliant electronic records and signatures.
- Practical Examples: Review practical examples covering the implementation of FDA requirements.
- Data Integrity: Understand the need for data integrity throughout the system and data life cycles and how to maintain it.
- Cloud Computing and Mobile Applications: Learn approaches to cloud computing and mobile applications in the GxP environment.
EMA Annex 11 Learning Objectives
- General Guidance: Understand the general guidance on managing risks, personnel responsibilities, and working with third-party suppliers and service providers.
- Validation: Learn best practices for validation and what should be included in validation documentation.
- Operational Phase: During the operational phase, gain knowledge on data management, security, and risk minimization for computerized systems.
- Electronic Signatures: Understand the requirements for electronic signatures and how they should be permanently linked to the respective record, including time and date.
- Audit Trails: Learn about the implementation and review of audit trails to ensure data integrity.
- Security Access: Understand the requirements for security access to protect electronic records and electronic signatures.
- Data Governance: Evaluate the requirements for a robust data governance system.
- Compliance with EU Regulations: Learn how to align with Annex 11 to ensure compliance with related EU regulations.
Course Outline: 21 CFR Part 11 and EMA Annex 11 for IT Professionals
Module 1: Introduction and Regulatory Overview
- History and background of 21 CFR Part 11 and EMA Annex 11
- Purpose and scope of the regulations
- Applicability to electronic records and electronic signatures
- Regulatory bodies and enforcement
Module 2: 21 CFR Part 11 Requirements
- Subpart A: General Provisions
- Definitions of key terms
- Implementation and scope
- Subpart B: Electronic Records
- Controls for closed and open systems
- Audit trails
- Operational and device checks
- Authority checks
- Record retention and availability
- Subpart C: Electronic Signatures
- General requirements
- Electronic signature components and controls
- Identification codes and passwords
Module 3: EMA Annex 11 Requirements
- General requirements
- Risk management
- Personnel roles and responsibilities
- Suppliers and service providers
- Project phase
- User requirements and specifications
- System design and development
- System validation
- Testing and release management
- Operational phase
- Data governance and integrity
- Audit trails and change control
- Periodic evaluations
- Security measures
- Electronic signatures
- Business continuity planning
Module 4: PIC/S Data Integrity Requirements
- Data Governance System
- Structure and control of the Quality Management System (QMS)
- Policies related to organizational values, quality, staff conduct, and ethics
- Organizational Influences
- Roles and responsibilities for data integrity
- Training and awareness programs
- General Data Integrity Principles
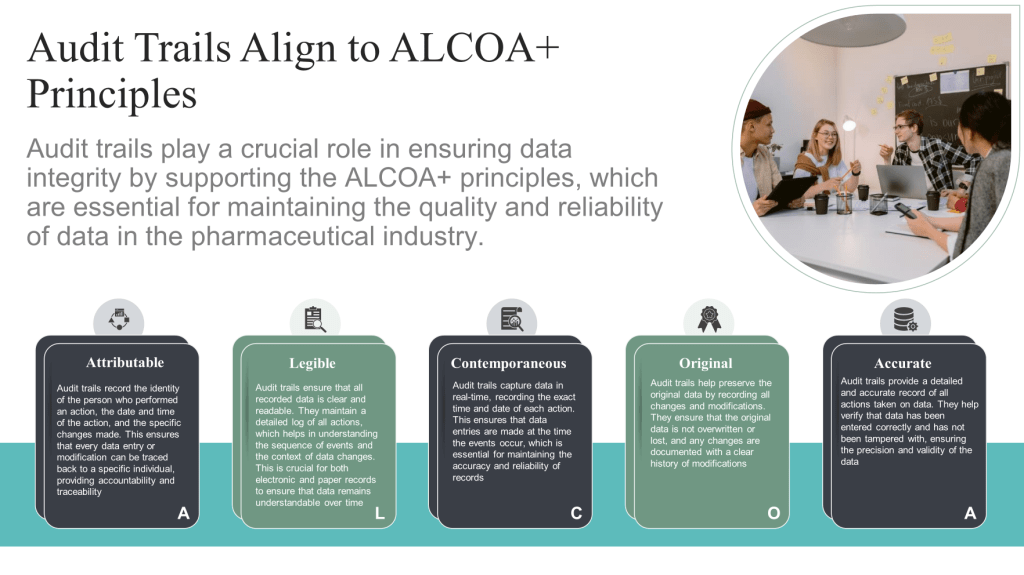
- ALCOA+ principles (Attributable, Legible, Contemporaneous, Original, Accurate, Complete, Consistent, Enduring, and Available)
- Data lifecycle management
- Specific Considerations for Computerized Systems
- Qualification and validation of computerized systems
- System security and access controls
- Audit trails and data review
- Management of hybrid systems
- Outsourced Activities
- Data integrity considerations for third-party suppliers
- Contractual agreements and oversight
- Regulatory Actions and Remediation
- Responding to data integrity issues
- Remediation strategies and corrective actions
- Periodic System Evaluation
- Regular reviews and re-validation
- Risk-based approach to system updates and maintenance
Module 5: Compliance Strategies and Best Practices
- Interpreting regulatory guidance documents
- Conducting risk assessments
- Our validation approach
- Leveraging suppliers and third-party service providers
- Implementing audit trails and electronic signatures
- Data integrity and security controls
- Change and configuration management
- Training and documentation requirements
Module 6: Case Studies and Industry Examples
- Review of FDA warning letters and 483 observations
- Lessons learned from industry compliance initiatives
- Practical examples of system validation and audits
Module 7: Future Trends and Developments
- Regulatory updates and revisions
- Impact of new technologies (AI, cloud, etc.)
- Harmonization efforts between global regulations
- Continuous compliance monitoring
The course will include interactive elements such as hands-on exercises, quizzes, and group discussions to reinforce the learning objectives. The course will provide practical insights for IT professionals by focusing on real-world examples from our company.