|
Requirement |
Description |
|
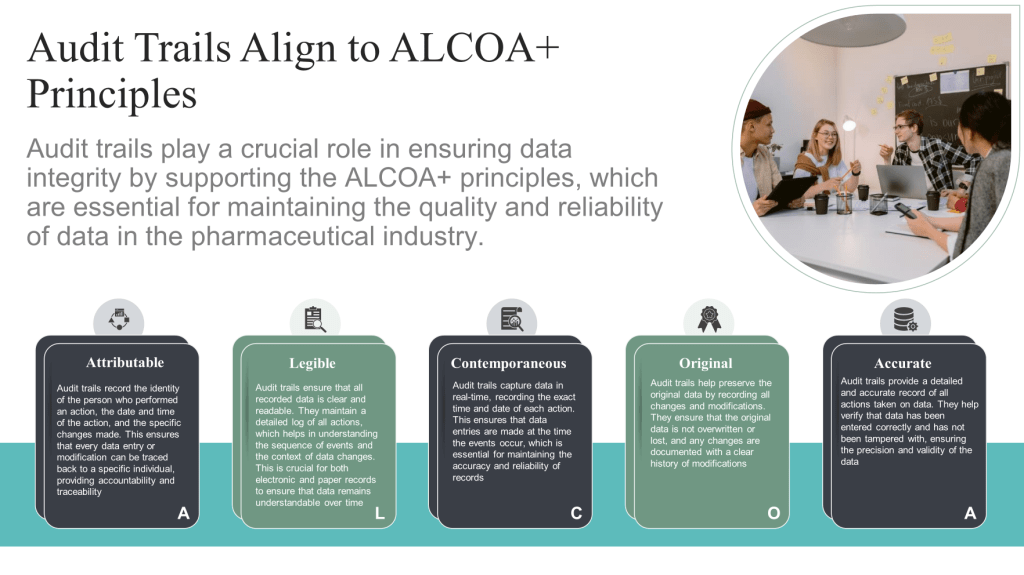
Attributable (Traceable) |
|
|
Legible |
|
|
Contemporaneous |
|
|
Original |
|
|
Accurate |
|
|
Complete |
|
|
Consistent |
|
|
Enduring |
|
|
Available |
|
21CFR Part 11 Requirements
Definition: An audit trail is a secure, computer-generated, time-stamped electronic record that allows for the reconstruction of events related to the creation, modification, and deletion of an electronic record.
Requirements:
- Availability: Audit trails must be easily accessible for review and copying by the FDA during inspections.
- Automation: Entries must be automatically captured by the system without manual intervention.
- Components: Each entry must include a timestamp, user ID, original and new values, and reasons for changes where applicable.
- Security: Audit trail data must be securely stored and not accessible for editing by users
EMA Annex 11 (Eudralex Volume 4) Requirements
Definition: Audit trails are records of all GMP-relevant changes and deletions, created by the system to ensure traceability and accountability.
Requirements:
- Risk-Based Approach: Building audit trails into the system for all GMP-relevant changes and deletions should be considered based on a risk assessment.
- Documentation: The reasons for changes or deletions must be documented.
- Review: Audit trails must be available, convertible into a generally readable form, and regularly reviewed.
- Validation: The audit trail functionality must be validated to ensure it captures all necessary data accurately and securely.
Requirements from PIC/S GMP Data Integrity Guidance
Definition: Audit trails are metadata recorded about critical information such as changes or deletions of GMP/GDP relevant data to enable the reconstruction of activities.
Requirements:
- Review: Critical audit trails related to each operation should be independently reviewed with all other records related to the operation, especially before batch release.
- Documentation: Significant deviations found during the audit trail review must be fully investigated and documented.